Where Does a Network Firewall Go? Network Perimeter Security
The firewall remains an essential component of any network. In this guide, we'll go through various network topologies and where a firewall is placed in each.
Nov 9, 2022
SHARE
The network firewall remains an essential component of almost any network structure. The need to minimize your organization’s exposure to outside threats and unauthorized connections is as critical as ever as cyber attacks gain momentum and hackers employ more advanced methods.
However, as network topologies continue to diversify, and user-friendly, software-based topologies like SD-WAN allow greater control over network infrastructure, it’s important to think carefully about how and where you place network firewalls to ensure perimeter security.
If a picture paints a thousand words, you’ll be glad we’ve enlisted our graphic designers to whip up some illustrations for this blog. I am kidding, as I made these myself (we don’t have designers sadly). It’s much easier to communicate network topologies visually.
We’ll start with the traditional “hub-and-spoke” network model, then look at a couple of MPLS-based topologies, before exploring some of the most common firewall deployments on an SD-WAN network.
Hub-and-Spoke Network
This first example shows a “classic” point-to-point, Hub-and-Spoke network. Let’s run through the main features defining the network firewall deployment.
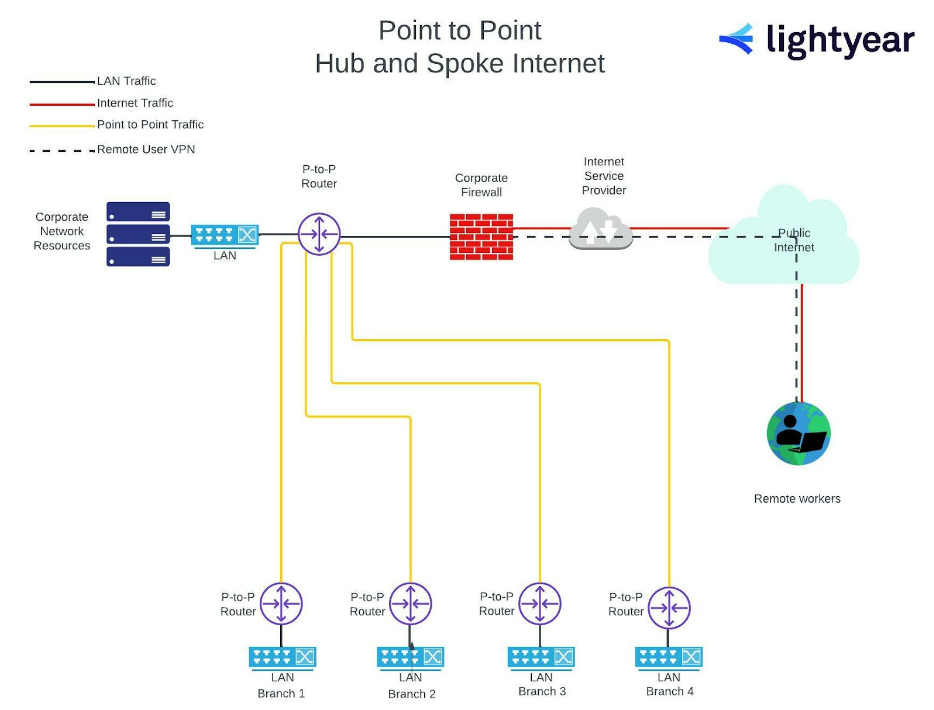
There’s no cloud-based infrastructure.
Everything resides on-site – file servers, print servers, SQL servers, application servers, even the domain controllers and DNS are on the premises.
Branch sites access the critical infrastructure of the corporate network resources via point-to-point circuits, eliminating the need for additional security in between.
Remote employees connect through a VPN over the public internet, meeting the firewall before accessing the corporate network.
So, with the traditional hub and spoke, the corporate network sits behind the network firewall.
MPLS Hub-and-Spoke Network
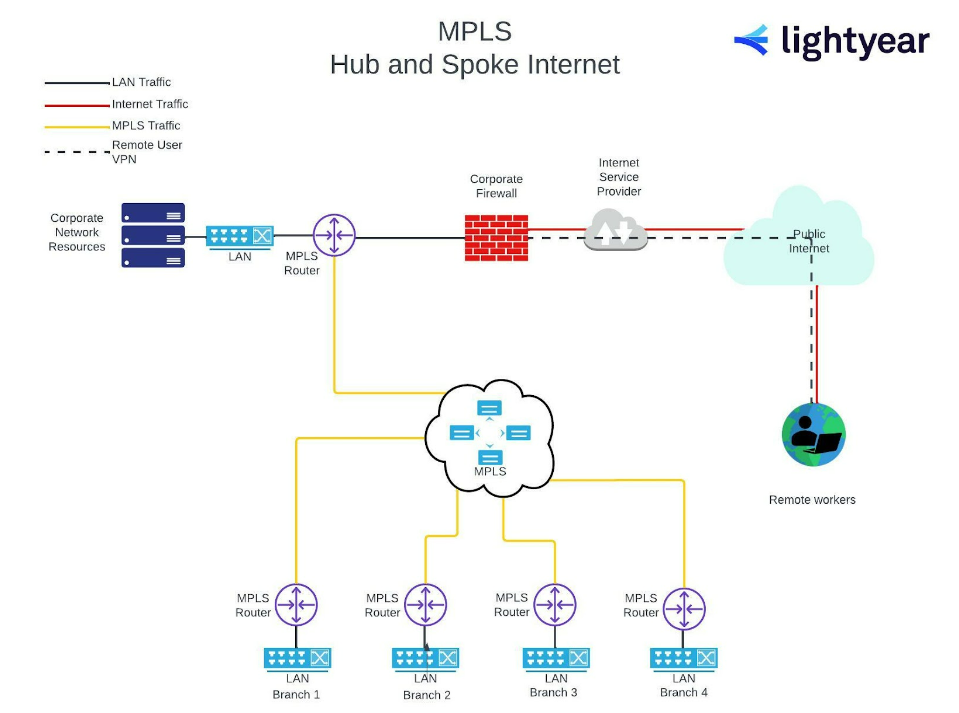
Hub-and-Spoke-style topologies can be built using Multi-Protocol Label Switching (MPLS), without creating significant security issues that would require a different network firewall configuration.
While traffic between the branch and corporate locations is no longer on point-to-point, the MPLS circuits are a secure, private network, partitioned from the public internet.
MPLS Distributed Internet
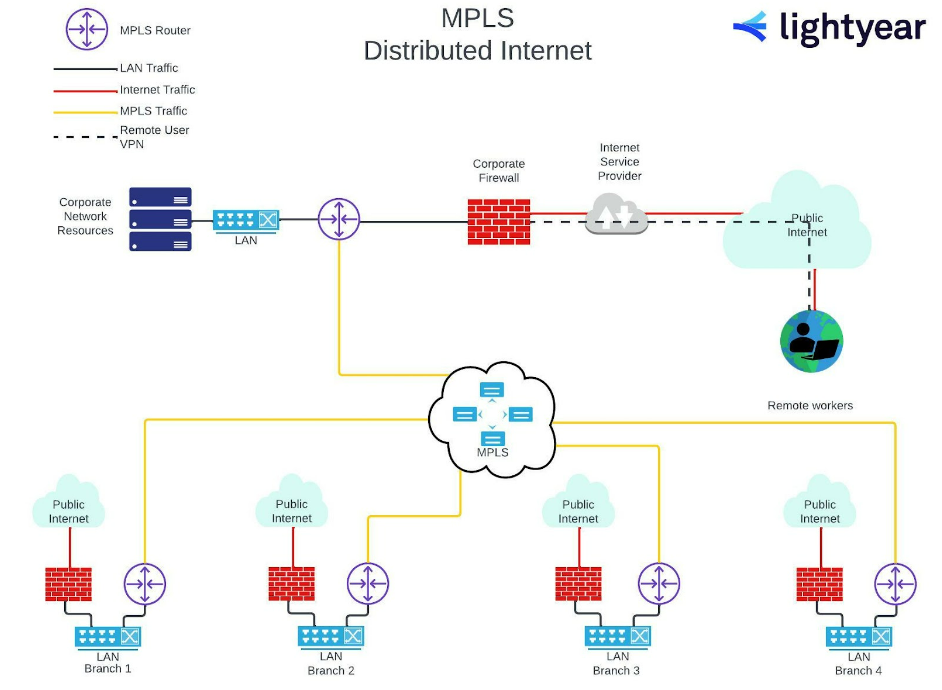
Other business needs, such as separate cloud-based services at the branch level, might require this common adaptation or MPLS-based network.
To implement this additional access to the public internet, each branch would require its own firewall as a default gateway.
The MPLS network structure would remain intact. Each branch would have the option of either accessing the public internet through their own firewall WAN connection, or connecting site-to-site across the LAN switch to the MPLS router’s LAN interface for private, secure data transfer.
SD-WAN
Ok, now it’s time to break out ALL the crayons and get artistic, as we delve into the most common SD-WAN deployment models.
The flexibility is kind of the point with SD WAN, and here at Lightyear we’ve seen some weird and wonderful network topologies created using SD WAN. Nevertheless, most network firewall deployment models can be safely grouped into one of these three categories.
Category 1 = the edge appliances setup networking directly to each other.
Category 2 = the edge appliances setup networking to a middle-mile network
Category 3 = the edge appliances setup networking to a secure middle-mile network
If you’re designing an SD WAN topology, it’s really useful to look at these three models and figure out which is the best starting point for your network design.
SD-WAN Firewall Deployment – Category 1
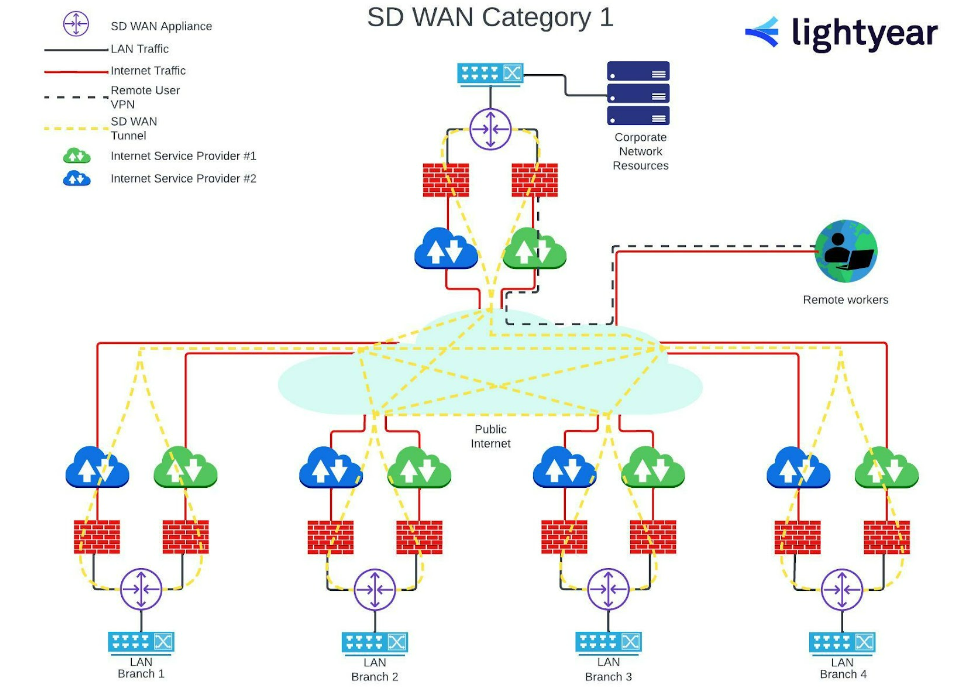
As you can see, public internet connects the branches to the corporate network and each other, which is usually provided on SD-WAN by multiple ISPs. This “provider agnostic” structure allows each branch to choose the best ISP for their location and requirements, potentially reducing costs and maximizing throughput at each site.
This dependence on the public internet means an increased reliance on separate network firewalls across the corporate network – each instance of an ISP provision will need its own firewall.
(Notice that the remote workers are still connecting to the central corporate network hub via a VPN, as they did under the Hub-and-Spoke models.)
SD-WAN Firewall Deployment – Category 2
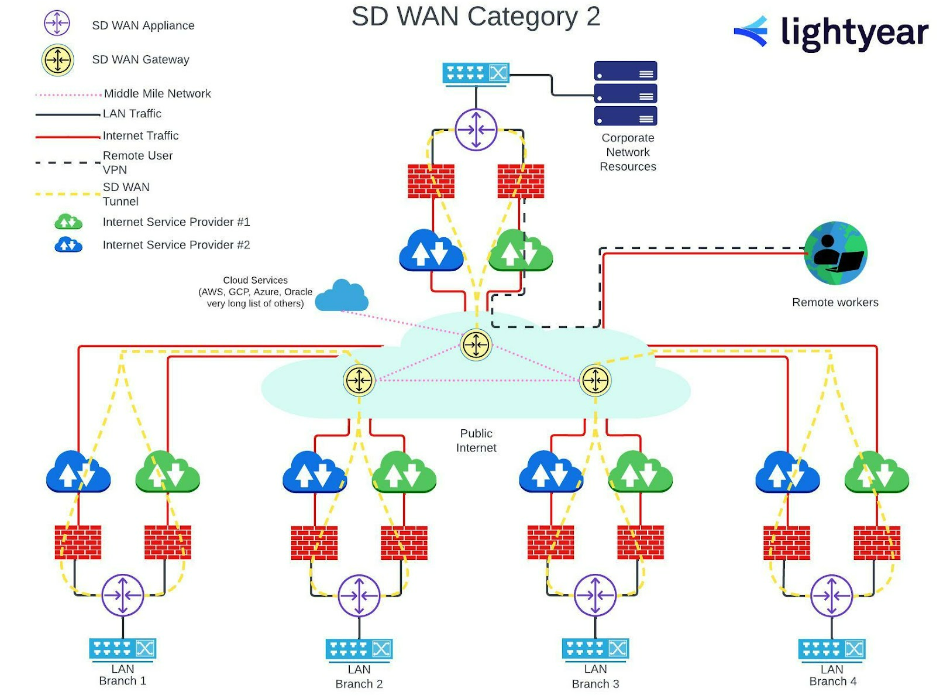
Category 2 allows for greater reliance on shared cloud services, distributed via a middle-mile network, which offers greater consistency of throughput for these services across all locations.
As in Category 1, each ISP connection requires a separate network firewall. The remote user’s VPN is now routed via the middle-mile network to allow them equal access to the cloud services.
SD-WAN Firewall Deployment – Category 3
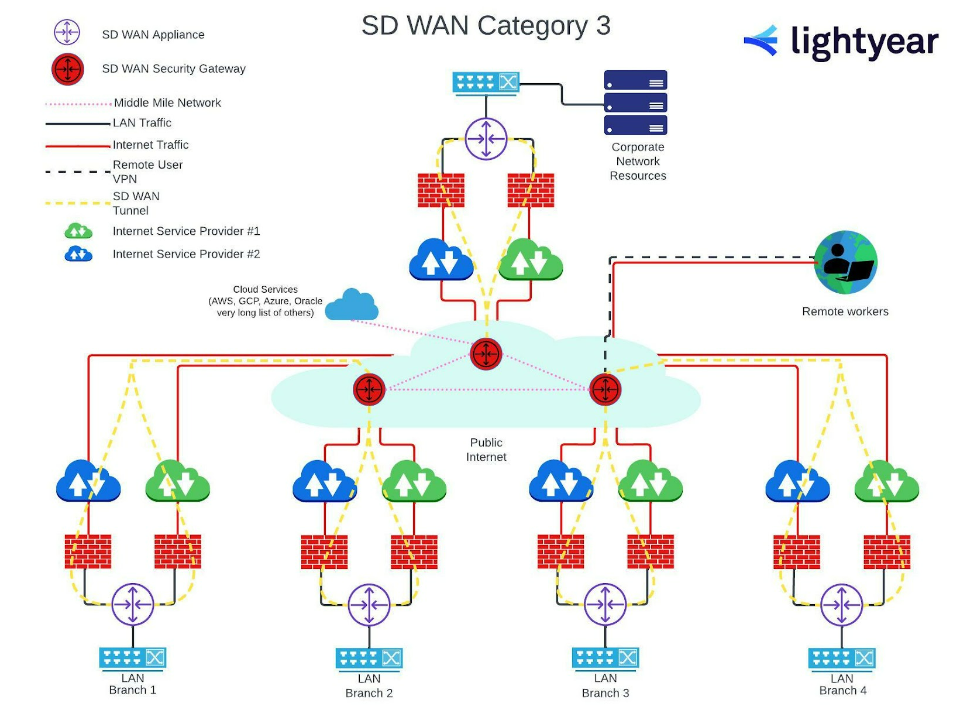
Category 3 topologies are broadly similar to Category 2 – the individual ISP connections still require firewall protection at the branch level, but security in the middle mile is now beefed up by SD-WAN security gateways, providing that secure middle mile.
There’s less reliance on the VPN for remote workers in this scenario – once they hit the middle mile, they can be routed along the same network as everybody else.
We’ve covered a lot of ground here, to show you the basics of firewall deployment across different network topologies. These are broad strokes, though, and it’s a good idea to discuss your specific connectivity and security requirements with a network professional. Here at Lightyear our team is happy and ready to work with you, even if you just need someone to chat through the options.
Want to learn more about how Lightyear can help you?
Let us show you the product and discuss specifics on how it might be helpful.
Not ready to buy?
Stay up to date on our product, straight to your inbox every month.
